
Computers, Materials & Continua is a peer-reviewed Open Access journal that publishes all types of academic papers in the areas of computer networks, artificial intelligence, big data, software engineering, multimedia, cyber security, internet of things, materials genome, integrated materials science, and data analysis, modeling, designing and manufacturing of modern functional and multifunctional materials. This journal is published monthly by Tech Science Press.
SCI: 2022 Impact Factor 3.1; Scopus CiteScore (Impact per Publication 2022): 5.0; SNIP (Source Normalized Impact per Paper 2022): 1.080; Ei Compendex; Cambridge Scientific Abstracts; INSPEC Databases; Science Navigator; EBSCOhost; ProQuest Central; Zentralblatt für Mathematik; Portico, etc.
 Refers to the articles published on the journal within the last three years that have gained the most viewing times to date (Statistics provided by TSP database)
Refers to the articles published on the journal within the last three years that have gained the most viewing times to date (Statistics provided by TSP database)
 Refers to articles published on the journal since 2020 that have received the most frequent citation to date (Statistics provided by TSP database)
Refers to articles published on the journal since 2020 that have received the most frequent citation to date (Statistics provided by TSP database)
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 1757-1773, 2024, DOI:10.32604/cmc.2024.049477
(This article belongs to the Special Issue: Advanced Machine Learning and Optimization for Practical Solutions in Complex Real-world Systems)
Abstract This research focuses on addressing the challenges associated with image detection in low-light environments, particularly by applying artificial intelligence techniques to machine vision and object recognition systems. The primary goal is to tackle issues related to recognizing objects with low brightness levels. In this study, the Intel RealSense Lidar Camera L515 is used to simultaneously capture color information and 16-bit depth information images. The detection scenarios are categorized into normal brightness and low brightness situations. When the system determines a normal brightness environment, normal brightness images are recognized using deep learning methods. In low-brightness situations, three methods are proposed for… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 1775-1794, 2024, DOI:10.32604/cmc.2024.049276
Abstract Monitoring blood pressure is a critical aspect of safeguarding an individual’s health, as early detection of abnormal blood pressure levels facilitates timely medical intervention, ultimately leading to a reduction in mortality rates associated with cardiovascular diseases. Consequently, the development of a robust and continuous blood pressure monitoring system holds paramount significance. In the context of this research paper, we introduce an innovative deep learning regression model that harnesses phonocardiogram (PCG) data to achieve precise blood pressure estimation. Our novel approach incorporates a convolutional neural network (CNN)-based regression model, which not only enhances its adaptability to spatial variations but also empowers… More >
 Open Access
Open Access
REVIEW
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 1795-1834, 2024, DOI:10.32604/cmc.2024.049846
Abstract The proliferation of IoT devices requires innovative approaches to gaining insights while preserving privacy and resources amid unprecedented data generation. However, FL development for IoT is still in its infancy and needs to be explored in various areas to understand the key challenges for deployment in real-world scenarios. The paper systematically reviewed the available literature using the PRISMA guiding principle. The study aims to provide a detailed overview of the increasing use of FL in IoT networks, including the architecture and challenges. A systematic review approach is used to collect, categorize and analyze FL-IoT-based articles. A search was performed in… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 1835-1854, 2024, DOI:10.32604/cmc.2024.049207
(This article belongs to the Special Issue: Advanced Machine Learning and Optimization for Practical Solutions in Complex Real-world Systems)
Abstract The Internet of Things (IoT) has witnessed a significant surge in adoption, particularly through the utilization of Wireless Sensor Networks (WSNs), which comprise small internet-connected devices. These deployments span various environments and offer a multitude of benefits. However, the widespread use of battery-powered devices introduces challenges due to their limited hardware resources and communication capabilities. In response to this, the Internet Engineering Task Force (IETF) has developed the IPv6 Routing Protocol for Low-power and Lossy Networks (RPL) to address the unique requirements of such networks. Recognizing the critical role of RPL in maintaining high performance, this paper proposes a novel… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 1855-1874, 2024, DOI:10.32604/cmc.2024.049480
(This article belongs to the Special Issue: Metaheuristic-Driven Optimization Algorithms: Methods and Applications)
Abstract This study focuses on the scheduling problem of unrelated parallel batch processing machines (BPM) with release times, a scenario derived from the moulding process in a foundry. In this process, a batch is initially formed, placed in a sandbox, and then the sandbox is positioned on a BPM for moulding. The complexity of the scheduling problem increases due to the consideration of BPM capacity and sandbox volume. To minimize the makespan, a new cooperated imperialist competitive algorithm (CICA) is introduced. In CICA, the number of empires is not a parameter, and four empires are maintained throughout the search process. Two… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 1875-1901, 2024, DOI:10.32604/cmc.2024.047961
Abstract Breast cancer detection heavily relies on medical imaging, particularly ultrasound, for early diagnosis and effective treatment. This research addresses the challenges associated with computer-aided diagnosis (CAD) of breast cancer from ultrasound images. The primary challenge is accurately distinguishing between malignant and benign tumors, complicated by factors such as speckle noise, variable image quality, and the need for precise segmentation and classification. The main objective of the research paper is to develop an advanced methodology for breast ultrasound image classification, focusing on speckle noise reduction, precise segmentation, feature extraction, and machine learning-based classification. A unique approach is introduced that combines Enhanced… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 1903-1923, 2024, DOI:10.32604/cmc.2024.049260
Abstract Traffic in today’s cities is a serious problem that increases travel times, negatively affects the environment, and drains financial resources. This study presents an Artificial Intelligence (AI) augmented Mobile Ad Hoc Networks (MANETs) based real-time prediction paradigm for urban traffic challenges. MANETs are wireless networks that are based on mobile devices and may self-organize. The distributed nature of MANETs and the power of AI approaches are leveraged in this framework to provide reliable and timely traffic congestion forecasts. This study suggests a unique Chaotic Spatial Fuzzy Polynomial Neural Network (CSFPNN) technique to assess real-time data acquired from various sources within… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 1925-1938, 2024, DOI:10.32604/cmc.2024.050899
(This article belongs to the Special Issue: Security, Privacy, and Robustness for Trustworthy AI Systems)
Abstract This paper proposes an artificial intelligence-based robust information hiding algorithm to address the issue of confidential information being susceptible to noise attacks during transmission. The algorithm we designed aims to mitigate the impact of various noise attacks on the integrity of secret information during transmission. The method we propose involves encoding secret images into stylized encrypted images and applies adversarial transfer to both the style and content features of the original and embedded data. This process effectively enhances the concealment and imperceptibility of confidential information, thereby improving the security of such information during transmission and reducing security risks. Furthermore, we… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 1939-1956, 2024, DOI:10.32604/cmc.2024.048135
(This article belongs to the Special Issue: The Next-generation Deep Learning Approaches to Emerging Real-world Applications)
Abstract The advent of self-attention mechanisms within Transformer models has significantly propelled the advancement of deep learning algorithms, yielding outstanding achievements across diverse domains. Nonetheless, self-attention mechanisms falter when applied to datasets with intricate semantic content and extensive dependency structures. In response, this paper introduces a Diffusion Sampling and Label-Driven Co-attention Neural Network (DSLD), which adopts a diffusion sampling method to capture more comprehensive semantic information of the data. Additionally, the model leverages the joint correlation information of labels and data to introduce the computation of text representation, correcting semantic representation biases in the data, and increasing the accuracy of semantic… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 1957-1974, 2024, DOI:10.32604/cmc.2024.048956
Abstract As cloud quantum computing gains broader acceptance, a growing quantity of researchers are directing their focus towards this domain. Nevertheless, the rapid surge in demand for cloud-based quantum computing resources has led to a scarcity, which in turn hampers users from achieving optimal satisfaction. Therefore, cloud quantum computing service providers require a unified analysis and scheduling framework for their quantum resources and user jobs to meet the ever-growing usage demands. This paper introduces a new multi-programming scheduling framework for quantum computing in a cloud environment. The framework addresses the issue of limited quantum computing resources in cloud environments and ensures… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 1975-1994, 2024, DOI:10.32604/cmc.2024.049228
(This article belongs to the Special Issue: Advanced Machine Learning and Optimization for Practical Solutions in Complex Real-world Systems)
Abstract Brain tumors come in various types, each with distinct characteristics and treatment approaches, making manual detection a time-consuming and potentially ambiguous process. Brain tumor detection is a valuable tool for gaining a deeper understanding of tumors and improving treatment outcomes. Machine learning models have become key players in automating brain tumor detection. Gradient descent methods are the mainstream algorithms for solving machine learning models. In this paper, we propose a novel distributed proximal stochastic gradient descent approach to solve the L-Smooth Support Vector Machine (SVM) classifier for brain tumor detection. Firstly, the smooth hinge loss is introduced to be used… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 1995-2014, 2024, DOI:10.32604/cmc.2024.048238
Abstract The motivation for this study is that the quality of deep fakes is constantly improving, which leads to the need to develop new methods for their detection. The proposed Customized Convolutional Neural Network method involves extracting structured data from video frames using facial landmark detection, which is then used as input to the CNN. The customized Convolutional Neural Network method is the date augmented-based CNN model to generate ‘fake data’ or ‘fake images’. This study was carried out using Python and its libraries. We used 242 films from the dataset gathered by the Deep Fake Detection Challenge, of which 199… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2015-2034, 2024, DOI:10.32604/cmc.2024.048527
(This article belongs to the Special Issue: Machine Vision Detection and Intelligent Recognition)
Abstract Recognizing handwritten characters remains a critical and formidable challenge within the realm of computer vision. Although considerable strides have been made in enhancing English handwritten character recognition through various techniques, deciphering Arabic handwritten characters is particularly intricate. This complexity arises from the diverse array of writing styles among individuals, coupled with the various shapes that a single character can take when positioned differently within document images, rendering the task more perplexing. In this study, a novel segmentation method for Arabic handwritten scripts is suggested. This work aims to locate the local minima of the vertical and diagonal word image densities… More >
 Open Access
Open Access
REVIEW
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2035-2062, 2024, DOI:10.32604/cmc.2024.049970
Abstract Border Gateway Protocol (BGP) is a standard inter-domain routing protocol for the Internet that conveys network layer reachability information and establishes routes to different destinations. The BGP protocol exhibits security design defects, such as an unconditional trust mechanism and the default acceptance of BGP route announcements from peers by BGP neighboring nodes, easily triggering prefix hijacking, path forgery, route leakage, and other BGP security threats. Meanwhile, the traditional BGP security mechanism, relying on a public key infrastructure, faces issues like a single point of failure and a single point of trust. The decentralization, anti-tampering, and traceability advantages of blockchain offer… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2063-2083, 2024, DOI:10.32604/cmc.2024.049147
Abstract The presence of numerous uncertainties in hybrid decision information systems (HDISs) renders attribute reduction a formidable task. Currently available attribute reduction algorithms, including those based on Pawlak attribute importance, Skowron discernibility matrix, and information entropy, struggle to effectively manages multiple uncertainties simultaneously in HDISs like the precise measurement of disparities between nominal attribute values, and attributes with fuzzy boundaries and abnormal values. In order to address the aforementioned issues, this paper delves into the study of attribute reduction within HDISs. First of all, a novel metric based on the decision attribute is introduced to solve the problem of accurately measuring… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2085-2103, 2024, DOI:10.32604/cmc.2024.048095
(This article belongs to the Special Issue: Multimedia Encryption and Information Security)
Abstract Among steganalysis techniques, detection against MV (motion vector) domain-based video steganography in the HEVC (High Efficiency Video Coding) standard remains a challenging issue. For the purpose of improving the detection performance, this paper proposes a steganalysis method that can perfectly detect MV-based steganography in HEVC. Firstly, we define the local optimality of MVP (Motion Vector Prediction) based on the technology of AMVP (Advanced Motion Vector Prediction). Secondly, we analyze that in HEVC video, message embedding either using MVP index or MVD (Motion Vector Difference) may destroy the above optimality of MVP. And then, we define the optimal rate of MVP… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2105-2122, 2024, DOI:10.32604/cmc.2024.048928
Abstract Crowd counting is a promising hotspot of computer vision involving crowd intelligence analysis, achieving tremendous success recently with the development of deep learning. However, there have been still many challenges including crowd multi-scale variations and high network complexity, etc. To tackle these issues, a lightweight Res-connection multi-branch network (LRMBNet) for highly accurate crowd counting and localization is proposed. Specifically, using improved ShuffleNet V2 as the backbone, a lightweight shallow extractor has been designed by employing the channel compression mechanism to reduce enormously the number of network parameters. A light multi-branch structure with different expansion rate convolutions is demonstrated to extract… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2123-2149, 2024, DOI:10.32604/cmc.2024.048914
Abstract Mobile banking security has witnessed significant R&D attention from both financial institutions and academia. This is due to the growing number of mobile baking applications and their reachability and usefulness to society. However, these applications are also attractive prey for cybercriminals, who use a variety of malware to steal personal banking information. Related literature in mobile banking security requires many permissions that are not necessary for the application’s intended security functionality. In this context, this paper presents a novel efficient permission identification approach for securing mobile banking (MoBShield) to detect and prevent malware. A permission-based dataset is generated for mobile… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2151-2168, 2024, DOI:10.32604/cmc.2024.049360
(This article belongs to the Special Issue: Advances and Applications in Signal, Image and Video Processing)
Abstract Hyperspectral imagery encompasses spectral and spatial dimensions, reflecting the material properties of objects. Its application proves crucial in search and rescue, concealed target identification, and crop growth analysis. Clustering is an important method of hyperspectral analysis. The vast data volume of hyperspectral imagery, coupled with redundant information, poses significant challenges in swiftly and accurately extracting features for subsequent analysis. The current hyperspectral feature clustering methods, which are mostly studied from space or spectrum, do not have strong interpretability, resulting in poor comprehensibility of the algorithm. So, this research introduces a feature clustering algorithm for hyperspectral imagery from an interpretability perspective.… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2169-2186, 2024, DOI:10.32604/cmc.2024.049645
(This article belongs to the Special Issue: Advanced Artificial Intelligence and Machine Learning Frameworks for Signal and Image Processing Applications)
Abstract Face recognition (FR) technology has numerous applications in artificial intelligence including biometrics, security, authentication, law enforcement, and surveillance. Deep learning (DL) models, notably convolutional neural networks (CNNs), have shown promising results in the field of FR. However CNNs are easily fooled since they do not encode position and orientation correlations between features. Hinton et al. envisioned Capsule Networks as a more robust design capable of retaining pose information and spatial correlations to recognize objects more like the brain does. Lower-level capsules hold 8-dimensional vectors of attributes like position, hue, texture, and so on, which are routed to higher-level capsules via… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2187-2207, 2024, DOI:10.32604/cmc.2024.048859
(This article belongs to the Special Issue: Intelligent Computing Techniques and Their Real Life Applications)
Abstract In the process of identifying parameters for a permanent magnet synchronous motor, the particle swarm optimization method is prone to being stuck in local optima in the later stages of iteration, resulting in low parameter accuracy. This work proposes a fuzzy particle swarm optimization approach based on the transformation function and the filled function. This approach addresses the topic of particle swarm optimization in parameter identification from two perspectives. Firstly, the algorithm uses a transformation function to change the form of the fitness function without changing the position of the extreme point of the fitness function, making the extreme point… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2209-2228, 2024, DOI:10.32604/cmc.2024.050585
Abstract Text classification, by automatically categorizing texts, is one of the foundational elements of natural language processing applications. This study investigates how text classification performance can be improved through the integration of entity-relation information obtained from the Wikidata (Wikipedia database) database and BERT-based pre-trained Named Entity Recognition (NER) models. Focusing on a significant challenge in the field of natural language processing (NLP), the research evaluates the potential of using entity and relational information to extract deeper meaning from texts. The adopted methodology encompasses a comprehensive approach that includes text preprocessing, entity detection, and the integration of relational information. Experiments conducted on… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2229-2251, 2024, DOI:10.32604/cmc.2024.047438
Abstract Medical Internet of Things (IoT) devices are becoming more and more common in healthcare. This has created a huge need for advanced predictive health modeling strategies that can make good use of the growing amount of multimodal data to find potential health risks early and help individuals in a personalized way. Existing methods, while useful, have limitations in predictive accuracy, delay, personalization, and user interpretability, requiring a more comprehensive and efficient approach to harness modern medical IoT devices. MAIPFE is a multimodal approach integrating pre-emptive analysis, personalized feature selection, and explainable AI for real-time health monitoring and disease detection. By… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2253-2276, 2024, DOI:10.32604/cmc.2024.049504
Abstract Website fingerprinting, also known as WF, is a traffic analysis attack that enables local eavesdroppers to infer a user’s browsing destination, even when using the Tor anonymity network. While advanced attacks based on deep neural network (DNN) can perform feature engineering and attain accuracy rates of over 98%, research has demonstrated that DNN is vulnerable to adversarial samples. As a result, many researchers have explored using adversarial samples as a defense mechanism against DNN-based WF attacks and have achieved considerable success. However, these methods suffer from high bandwidth overhead or require access to the target model, which is unrealistic. This… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2277-2293, 2024, DOI:10.32604/cmc.2024.047989
(This article belongs to the Special Issue: Recent Advances in Ensemble Framework of Meta-heuristics and Machine Learning: Methods and Applications)
Abstract Radiomics is a non-invasive method for extracting quantitative and higher-dimensional features from medical images for diagnosis. It has received great attention due to its huge application prospects in recent years. We can know that the number of features selected by the existing radiomics feature selection methods is basically about ten. In this paper, a heuristic feature selection method based on frequency iteration and multiple supervised training mode is proposed. Based on the combination between features, it decomposes all features layer by layer to select the optimal features for each layer, then fuses the optimal features to form a local optimal… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2295-2313, 2024, DOI:10.32604/cmc.2024.047754
Abstract Many deep learning-based registration methods rely on a single-stream encoder-decoder network for computing deformation fields between 3D volumes. However, these methods often lack constraint information and overlook semantic consistency, limiting their performance. To address these issues, we present a novel approach for medical image registration called the Dual-VoxelMorph, featuring a dual-channel cross-constraint network. This innovative network utilizes both intensity and segmentation images, which share identical semantic information and feature representations. Two encoder-decoder structures calculate deformation fields for intensity and segmentation images, as generated by the dual-channel cross-constraint network. This design facilitates bidirectional communication between grayscale and segmentation information, enabling the… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2315-2329, 2024, DOI:10.32604/cmc.2024.048443
Abstract Aiming at the problems of low accuracy and slow convergence speed of current intrusion detection models, SpiralConvolution is combined with Long Short-Term Memory Network to construct a new intrusion detection model. The dataset is first preprocessed using solo thermal encoding and normalization functions. Then the spiral convolution-Long Short-Term Memory Network model is constructed, which consists of spiral convolution, a two-layer long short-term memory network, and a classifier. It is shown through experiments that the model is characterized by high accuracy, small model computation, and fast convergence speed relative to previous deep learning models. The model uses a new neural network… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2331-2359, 2024, DOI:10.32604/cmc.2024.047275
Abstract Adversarial distillation (AD) has emerged as a potential solution to tackle the challenging optimization problem of loss with hard labels in adversarial training. However, fixed sample-agnostic and student-egocentric attack strategies are unsuitable for distillation. Additionally, the reliability of guidance from static teachers diminishes as target models become more robust. This paper proposes an AD method called Learnable Distillation Attack Strategies and Evolvable Teachers Adversarial Distillation (LDAS&ET-AD). Firstly, a learnable distillation attack strategies generating mechanism is developed to automatically generate sample-dependent attack strategies tailored for distillation. A strategy model is introduced to produce attack strategies that enable adversarial examples (AEs) to… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2361-2373, 2024, DOI:10.32604/cmc.2024.049159
(This article belongs to the Special Issue: Security, Privacy, and Robustness for Trustworthy AI Systems)
Abstract Federated learning ensures data privacy and security by sharing models among multiple computing nodes instead of plaintext data. However, there is still a potential risk of privacy leakage, for example, attackers can obtain the original data through model inference attacks. Therefore, safeguarding the privacy of model parameters becomes crucial. One proposed solution involves incorporating homomorphic encryption algorithms into the federated learning process. However, the existing federated learning privacy protection scheme based on homomorphic encryption will greatly reduce the efficiency and robustness when there are performance differences between parties or abnormal nodes. To solve the above problems, this paper proposes a… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2375-2398, 2024, DOI:10.32604/cmc.2024.048112
(This article belongs to the Special Issue: Industrial Big Data and Artificial Intelligence-Driven Intelligent Perception, Maintenance, and Decision Optimization in Industrial Systems)
Abstract Due to the time-varying topology and possible disturbances in a conflict environment, it is still challenging to maintain the mission performance of flying Ad hoc networks (FANET), which limits the application of Unmanned Aerial Vehicle (UAV) swarms in harsh environments. This paper proposes an intelligent framework to quickly recover the cooperative coverage mission by aggregating the historical spatio-temporal network with the attention mechanism. The mission resilience metric is introduced in conjunction with connectivity and coverage status information to simplify the optimization model. A spatio-temporal node pooling method is proposed to ensure all node location features can be updated after destruction… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2399-2425, 2024, DOI:10.32604/cmc.2024.049704
Abstract Genetic algorithms (GAs) are very good metaheuristic algorithms that are suitable for solving NP-hard combinatorial optimization problems. A simple GA begins with a set of solutions represented by a population of chromosomes and then uses the idea of survival of the fittest in the selection process to select some fitter chromosomes. It uses a crossover operator to create better offspring chromosomes and thus, converges the population. Also, it uses a mutation operator to explore the unexplored areas by the crossover operator, and thus, diversifies the GA search space. A combination of crossover and mutation operators makes the GA search strong… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2427-2448, 2024, DOI:10.32604/cmc.2024.047326
Abstract Facial emotion recognition (FER) has become a focal point of research due to its widespread applications, ranging from human-computer interaction to affective computing. While traditional FER techniques have relied on handcrafted features and classification models trained on image or video datasets, recent strides in artificial intelligence and deep learning (DL) have ushered in more sophisticated approaches. The research aims to develop a FER system using a Faster Region Convolutional Neural Network (FRCNN) and design a specialized FRCNN architecture tailored for facial emotion recognition, leveraging its ability to capture spatial hierarchies within localized regions of facial features. The proposed work enhances… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2449-2463, 2024, DOI:10.32604/cmc.2024.050425
Abstract Cloud computing has emerged as a viable alternative to traditional computing infrastructures, offering various benefits. However, the adoption of cloud storage poses significant risks to data secrecy and integrity. This article presents an effective mechanism to preserve the secrecy and integrity of data stored on the public cloud by leveraging blockchain technology, smart contracts, and cryptographic primitives. The proposed approach utilizes a Solidity-based smart contract as an auditor for maintaining and verifying the integrity of outsourced data. To preserve data secrecy, symmetric encryption systems are employed to encrypt user data before outsourcing it. An extensive performance analysis is conducted to… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2465-2480, 2024, DOI:10.32604/cmc.2024.049605
Abstract The classification of functional data has drawn much attention in recent years. The main challenge is representing infinite-dimensional functional data by finite-dimensional features while utilizing those features to achieve better classification accuracy. In this paper, we propose a mean-variance-based (MV) feature weighting method for classifying functional data or functional curves. In the feature extraction stage, each sample curve is approximated by B-splines to transfer features to the coefficients of the spline basis. After that, a feature weighting approach based on statistical principles is introduced by comprehensively considering the between-class differences and within-class variations of the coefficients. We also introduce a… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2481-2503, 2024, DOI:10.32604/cmc.2024.050005
Abstract In the process of constructing domain-specific knowledge graphs, the task of relational triple extraction plays a critical role in transforming unstructured text into structured information. Existing relational triple extraction models face multiple challenges when processing domain-specific data, including insufficient utilization of semantic interaction information between entities and relations, difficulties in handling challenging samples, and the scarcity of domain-specific datasets. To address these issues, our study introduces three innovative components: Relation semantic enhancement, data augmentation, and a voting strategy, all designed to significantly improve the model’s performance in tackling domain-specific relational triple extraction tasks. We first propose an innovative attention interaction… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2505-2522, 2024, DOI:10.32604/cmc.2024.049898
(This article belongs to the Special Issue: Advanced Artificial Intelligence and Machine Learning Frameworks for Signal and Image Processing Applications)
Abstract Brain–computer interface (BCI) systems, such as the P300 speller, enable patients to express intentions without necessitating extensive training. However, the complexity of operational instructions and the slow pace of character spelling pose challenges for some patients. In this paper, an image segmentation P300 selector based on YOLOv7-mask and DeepSORT is proposed. The proposed system utilizes a camera to capture real-world objects for classification and tracking. By applying predefined stimulation rules and object-specific masks, the proposed system triggers stimuli associated with the objects displayed on the screen, inducing the generation of P300 signals in the patient’s brain. Its video processing mechanism… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2523-2546, 2024, DOI:10.32604/cmc.2024.047543
(This article belongs to the Special Issue: AI and Data Security for the Industrial Internet)
Abstract In order to enhance the accuracy of Air Traffic Control (ATC) cybersecurity attack detection, in this paper, a new clustering detection method is designed for air traffic control network security attacks. The feature set for ATC cybersecurity attacks is constructed by setting the feature states, adding recursive features, and determining the feature criticality. The expected information gain and entropy of the feature data are computed to determine the information gain of the feature data and reduce the interference of similar feature data. An autoencoder is introduced into the AI (artificial intelligence) algorithm to encode and decode the characteristics of ATC… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2547-2563, 2024, DOI:10.32604/cmc.2024.048755
(This article belongs to the Special Issue: Machine Vision Detection and Intelligent Recognition)
Abstract Remote sensing imagery, due to its high altitude, presents inherent challenges characterized by multiple scales, limited target areas, and intricate backgrounds. These inherent traits often lead to increased miss and false detection rates when applying object recognition algorithms tailored for remote sensing imagery. Additionally, these complexities contribute to inaccuracies in target localization and hinder precise target categorization. This paper addresses these challenges by proposing a solution: The YOLO-MFD model (YOLO-MFD: Remote Sensing Image Object Detection with Multi-scale Fusion Dynamic Head). Before presenting our method, we delve into the prevalent issues faced in remote sensing imagery analysis. Specifically, we emphasize the… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2565-2583, 2024, DOI:10.32604/cmc.2024.047597
(This article belongs to the Special Issue: Recent Advances in Ophthalmic Diseases Diagnosis using AI)
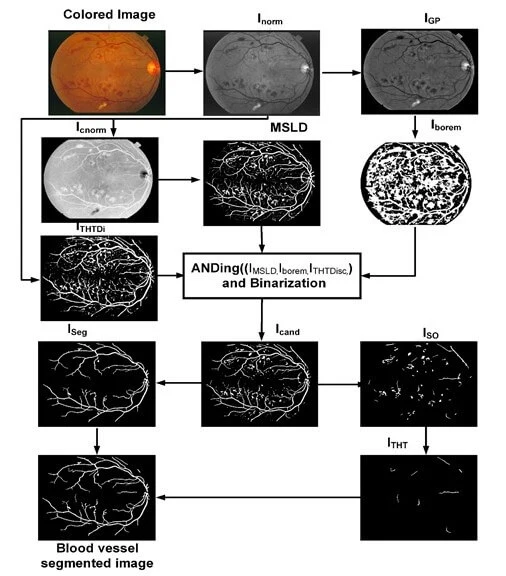
Abstract Diagnosing various diseases such as glaucoma, age-related macular degeneration, cardiovascular conditions, and diabetic retinopathy involves segmenting retinal blood vessels. The task is particularly challenging when dealing with color fundus images due to issues like non-uniform illumination, low contrast, and variations in vessel appearance, especially in the presence of different pathologies. Furthermore, the speed of the retinal vessel segmentation system is of utmost importance. With the surge of now available big data, the speed of the algorithm becomes increasingly important, carrying almost equivalent weightage to the accuracy of the algorithm. To address these challenges, we present a novel approach for retinal… More >
Graphic Abstract
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2585-2608, 2024, DOI:10.32604/cmc.2024.046461
(This article belongs to the Special Issue: Deep Learning in Medical Imaging-Disease Segmentation and Classification)
Abstract Augmentation of abnormal cells in the brain causes brain tumor (BT), and early screening and treatment will reduce its harshness in patients. BT’s clinical level screening is usually performed with Magnetic Resonance Imaging (MRI) due to its multi-modality nature. The overall aims of the study is to introduce, test and verify an advanced image processing technique with algorithms to automatically extract tumour sections from brain MRI scans, facilitating improved accuracy. The research intends to devise a reliable framework for detecting the BT region in the two-dimensional (2D) MRI slice, and identifying its class with improved accuracy. The methodology for the… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2609-2623, 2024, DOI:10.32604/cmc.2024.049611
(This article belongs to the Special Issue: Advanced Artificial Intelligence and Machine Learning Frameworks for Signal and Image Processing Applications)
Abstract The use of privacy-enhanced facial recognition has increased in response to growing concerns about data security and privacy in the digital age. This trend is spurred by rising demand for face recognition technology in a variety of industries, including access control, law enforcement, surveillance, and internet communication. However, the growing usage of face recognition technology has created serious concerns about data monitoring and user privacy preferences, especially in context-aware systems. In response to these problems, this study provides a novel framework that integrates sophisticated approaches such as Generative Adversarial Networks (GANs), Blockchain, and distributed computing to solve privacy concerns while… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2625-2646, 2024, DOI:10.32604/cmc.2024.050337
Abstract Images are the most important carrier of human information. Moreover, how to safely transmit digital images through public channels has become an urgent problem. In this paper, we propose a novel image encryption algorithm, called chaotic compressive sensing (CS) encryption (CCSE), which can not only improve the efficiency of image transmission but also introduce the high security of the chaotic system. Specifically, the proposed CCSE can fully leverage the advantages of the Chebyshev chaotic system and CS, enabling it to withstand various attacks, such as differential attacks, and exhibit robustness. First, we use a sparse trans-form to sparse the plaintext… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2647-2672, 2024, DOI:10.32604/cmc.2024.050380
(This article belongs to the Special Issue: Multi-Service and Resource Management in Intelligent Edge-Cloud Platform)
Abstract More devices in the Intelligent Internet of Things (AIoT) result in an increased number of tasks that require low latency and real-time responsiveness, leading to an increased demand for computational resources. Cloud computing’s low-latency performance issues in AIoT scenarios have led researchers to explore fog computing as a complementary extension. However, the effective allocation of resources for task execution within fog environments, characterized by limitations and heterogeneity in computational resources, remains a formidable challenge. To tackle this challenge, in this study, we integrate fog computing and cloud computing. We begin by establishing a fog-cloud environment framework, followed by the formulation… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2673-2696, 2024, DOI:10.32604/cmc.2024.049186
Abstract Cardiovascular disease is the leading cause of death globally. This disease causes loss of heart muscles and is also responsible for the death of heart cells, sometimes damaging their functionality. A person’s life may depend on receiving timely assistance as soon as possible. Thus, minimizing the death ratio can be achieved by early detection of heart attack (HA) symptoms. In the United States alone, an estimated 610,000 people die from heart attacks each year, accounting for one in every four fatalities. However, by identifying and reporting heart attack symptoms early on, it is possible to reduce damage and save many… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2697-2721, 2024, DOI:10.32604/cmc.2024.049607
(This article belongs to the Special Issue: Advanced Artificial Intelligence and Machine Learning Frameworks for Signal and Image Processing Applications)
Abstract Efficient optical network management poses significant importance in backhaul and access network communication for preventing service disruptions and ensuring Quality of Service (QoS) satisfaction. The emerging faults in optical networks introduce challenges that can jeopardize the network with a variety of faults. The existing literature witnessed various partial or inadequate solutions. On the other hand, Machine Learning (ML) has revolutionized as a promising technique for fault detection and prevention. Unlike traditional fault management systems, this research has three-fold contributions. First, this research leverages the ML and Deep Learning (DL) multi-classification system and evaluates their accuracy in detecting six distinct fault… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2723-2741, 2024, DOI:10.32604/cmc.2024.050344
Abstract With the explosive growth of false information on social media platforms, the automatic detection of multimodal false information has received increasing attention. Recent research has significantly contributed to multimodal information exchange and fusion, with many methods attempting to integrate unimodal features to generate multimodal news representations. However, they still need to fully explore the hierarchical and complex semantic correlations between different modal contents, severely limiting their performance detecting multimodal false information. This work proposes a two-stage detection framework for multimodal false information detection, called ASMFD, which is based on image aesthetic similarity to segment and explores the consistency and inconsistency… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2743-2769, 2024, DOI:10.32604/cmc.2024.049985
Abstract The Internet of Things (IoT) has characteristics such as node mobility, node heterogeneity, link heterogeneity, and topology heterogeneity. In the face of the IoT characteristics and the explosive growth of IoT nodes, which brings about large-scale data processing requirements, edge computing architecture has become an emerging network architecture to support IoT applications due to its ability to provide powerful computing capabilities and good service functions. However, the defense mechanism of Edge Computing-enabled IoT Nodes (ECIoTNs) is still weak due to their limited resources, so that they are susceptible to malicious software spread, which can compromise data confidentiality and network service… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2771-2793, 2024, DOI:10.32604/cmc.2024.046897
(This article belongs to the Special Issue: Requirements Engineering: Bridging Theory, Research and Practice)
Abstract Sentiment analysis is becoming increasingly important in today’s digital age, with social media being a significant source of user-generated content. The development of sentiment lexicons that can support languages other than English is a challenging task, especially for analyzing sentiment analysis in social media reviews. Most existing sentiment analysis systems focus on English, leaving a significant research gap in other languages due to limited resources and tools. This research aims to address this gap by building a sentiment lexicon for local languages, which is then used with a machine learning algorithm for efficient sentiment analysis. In the first step, a… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2795-2811, 2024, DOI:10.32604/cmc.2024.049410
(This article belongs to the Special Issue: Advanced Artificial Intelligence and Machine Learning Frameworks for Signal and Image Processing Applications)
Abstract Wheat is a critical crop, extensively consumed worldwide, and its production enhancement is essential to meet escalating demand. The presence of diseases like stem rust, leaf rust, yellow rust, and tan spot significantly diminishes wheat yield, making the early and precise identification of these diseases vital for effective disease management. With advancements in deep learning algorithms, researchers have proposed many methods for the automated detection of disease pathogens; however, accurately detecting multiple disease pathogens simultaneously remains a challenge. This challenge arises due to the scarcity of RGB images for multiple diseases, class imbalance in existing public datasets, and the difficulty… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2813-2831, 2024, DOI:10.32604/cmc.2024.050025
Abstract Federated learning is widely used to solve the problem of data decentralization and can provide privacy protection for data owners. However, since multiple participants are required in federated learning, this allows attackers to compromise. Byzantine attacks pose great threats to federated learning. Byzantine attackers upload maliciously created local models to the server to affect the prediction performance and training speed of the global model. To defend against Byzantine attacks, we propose a Byzantine robust federated learning scheme based on backdoor triggers. In our scheme, backdoor triggers are embedded into benign data samples, and then malicious local models can be identified… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2833-2850, 2024, DOI:10.32604/cmc.2024.046807
Abstract Spark, a distributed computing platform, has rapidly developed in the field of big data. Its in-memory computing feature reduces disk read overhead and shortens data processing time, making it have broad application prospects in large-scale computing applications such as machine learning and image processing. However, the performance of the Spark platform still needs to be improved. When a large number of tasks are processed simultaneously, Spark’s cache replacement mechanism cannot identify high-value data partitions, resulting in memory resources not being fully utilized and affecting the performance of the Spark platform. To address the problem that Spark’s default cache replacement algorithm… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2851-2878, 2024, DOI:10.32604/cmc.2024.050154
Abstract The increased adoption of Internet of Medical Things (IoMT) technologies has resulted in the widespread use of Body Area Networks (BANs) in medical and non-medical domains. However, the performance of IEEE 802.15.4-based BANs is impacted by challenges related to heterogeneous data traffic requirements among nodes, including contention during finite backoff periods, association delays, and traffic channel access through clear channel assessment (CCA) algorithms. These challenges lead to increased packet collisions, queuing delays, retransmissions, and the neglect of critical traffic, thereby hindering performance indicators such as throughput, packet delivery ratio, packet drop rate, and packet delay. Therefore, we propose Dynamic Next… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2879-2905, 2024, DOI:10.32604/cmc.2024.048725
(This article belongs to the Special Issue: Deep Learning in Computer-Aided Diagnosis Based on Medical Image)
Abstract Various deep learning models have been proposed for the accurate assisted diagnosis of early-stage Alzheimer’s disease (AD). Most studies predominantly employ Convolutional Neural Networks (CNNs), which focus solely on local features, thus encountering difficulties in handling global features. In contrast to natural images, Structural Magnetic Resonance Imaging (sMRI) images exhibit a higher number of channel dimensions. However, during the Position Embedding stage of Multi Head Self Attention (MHSA), the coded information related to the channel dimension is disregarded. To tackle these issues, we propose the RepBoTNet-CESA network, an advanced AD-aided diagnostic model that is capable of learning local and global… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2907-2922, 2024, DOI:10.32604/cmc.2024.050736
Abstract Concrete subjected to fire loads is susceptible to explosive spalling, which can lead to the exposure of reinforcing steel bars to the fire, substantially jeopardizing the structural safety and stability. The spalling of fire-loaded concrete is closely related to the evolution of pore pressure and temperature. Conventional analytical methods involve the resolution of complex, strongly coupled multifield equations, necessitating significant computational efforts. To rapidly and accurately obtain the distributions of pore-pressure and temperature, the Pix2Pix model is adopted in this work, which is celebrated for its capabilities in image generation. The open-source dataset used herein features RGB images we generated… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2923-2943, 2024, DOI:10.32604/cmc.2024.049139
(This article belongs to the Special Issue: Multimedia Encryption and Information Security)
Abstract In today’s rapidly evolving landscape of communication technologies, ensuring the secure delivery of sensitive data has become an essential priority. To overcome these difficulties, different steganography and data encryption methods have been proposed by researchers to secure communications. Most of the proposed steganography techniques achieve higher embedding capacities without compromising visual imperceptibility using LSB substitution. In this work, we have an approach that utilizes a combination of Most Significant Bit (MSB) matching and Least Significant Bit (LSB) substitution. The proposed algorithm divides confidential messages into pairs of bits and connects them with the MSBs of individual pixels using pair matching,… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2945-2970, 2024, DOI:10.32604/cmc.2024.050168
(This article belongs to the Special Issue: Advanced Artificial Intelligence and Machine Learning Frameworks for Signal and Image Processing Applications)
Abstract In pursuit of enhancing the Wireless Sensor Networks (WSNs) energy efficiency and operational lifespan, this paper delves into the domain of energy-efficient routing protocols. In WSNs, the limited energy resources of Sensor Nodes (SNs) are a big challenge for ensuring their efficient and reliable operation. WSN data gathering involves the utilization of a mobile sink (MS) to mitigate the energy consumption problem through periodic network traversal. The mobile sink (MS) strategy minimizes energy consumption and latency by visiting the fewest nodes or pre-determined locations called rendezvous points (RPs) instead of all cluster heads (CHs). CHs subsequently transmit packets to neighboring… More >
 Open Access
Open Access
REVIEW
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2971-2989, 2024, DOI:10.32604/cmc.2024.051289
Abstract In recent years, Non-Intrusive Load Monitoring (NILM) has become an emerging approach that provides affordable energy management solutions using aggregated load obtained from a single smart meter in the power grid. Furthermore, by integrating Machine Learning (ML), NILM can efficiently use electrical energy and offer less of a burden for the energy monitoring process. However, conducted research works have limitations for real-time implementation due to the practical issues. This paper aims to identify the contribution of ML approaches to developing a reliable Energy Management (EM) solution with NILM. Firstly, phases of the NILM are discussed, along with the research works… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 2991-3006, 2024, DOI:10.32604/cmc.2024.048637
Abstract With the rapid development of the mobile communication and the Internet, the previous web anomaly detection and identification models were built relying on security experts’ empirical knowledge and attack features. Although this approach can achieve higher detection performance, it requires huge human labor and resources to maintain the feature library. In contrast, semantic feature engineering can dynamically discover new semantic features and optimize feature selection by automatically analyzing the semantic information contained in the data itself, thus reducing dependence on prior knowledge. However, current semantic features still have the problem of semantic expression singularity, as they are extracted from a… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 3007-3021, 2024, DOI:10.32604/cmc.2024.051217
Abstract To enhance the efficiency and expediency of issuing e-licenses within the power sector, we must confront the challenge of managing the surging demand for data traffic. Within this realm, the network imposes stringent Quality of Service (QoS) requirements, revealing the inadequacies of traditional routing allocation mechanisms in accommodating such extensive data flows. In response to the imperative of handling a substantial influx of data requests promptly and alleviating the constraints of existing technologies and network congestion, we present an architecture for QoS routing optimization with in Software Defined Network (SDN), leveraging deep reinforcement learning. This innovative approach entails the separation… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 3023-3045, 2024, DOI:10.32604/cmc.2024.050281
Abstract The fast-paced development of blockchain technology is evident. Yet, the security concerns of smart contracts represent a significant challenge to the stability and dependability of the entire blockchain ecosystem. Conventional smart contract vulnerability detection primarily relies on static analysis tools, which are less efficient and accurate. Although deep learning methods have improved detection efficiency, they are unable to fully utilize the static relationships within contracts. Therefore, we have adopted the advantages of the above two methods, combining feature extraction mode of tools with deep learning techniques. Firstly, we have constructed corresponding feature extraction mode for different vulnerabilities, which are used… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 3047-3065, 2024, DOI:10.32604/cmc.2024.048901
(This article belongs to the Special Issue: Advances and Applications in Signal, Image and Video Processing)
Abstract Six degrees of freedom (6DoF) input interfaces are essential for manipulating virtual objects through translation or rotation in three-dimensional (3D) space. A traditional outside-in tracking controller requires the installation of expensive hardware in advance. While inside-out tracking controllers have been proposed, they often suffer from limitations such as interaction limited to the tracking range of the sensor (e.g., a sensor on the head-mounted display (HMD)) or the need for pose value modification to function as an input interface (e.g., a sensor on the controller). This study investigates 6DoF pose estimation methods without restricting the tracking range, using a smartphone as… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 3067-3087, 2024, DOI:10.32604/cmc.2024.049512
(This article belongs to the Special Issue: Advances and Applications in Signal, Image and Video Processing)
Abstract Regular exercise is a crucial aspect of daily life, as it enables individuals to stay physically active, lowers the likelihood of developing illnesses, and enhances life expectancy. The recognition of workout actions in video streams holds significant importance in computer vision research, as it aims to enhance exercise adherence, enable instant recognition, advance fitness tracking technologies, and optimize fitness routines. However, existing action datasets often lack diversity and specificity for workout actions, hindering the development of accurate recognition models. To address this gap, the Workout Action Video dataset (WAVd) has been introduced as a significant contribution. WAVd comprises a diverse… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 3089-3110, 2024, DOI:10.32604/cmc.2024.048133
(This article belongs to the Special Issue: Security, Privacy, and Robustness for Trustworthy AI Systems)
Abstract With the recent technological developments, massive vehicular ad hoc networks (VANETs) have been established, enabling numerous vehicles and their respective Road Side Unit (RSU) components to communicate with one another. The best way to enhance traffic flow for vehicles and traffic management departments is to share the data they receive. There needs to be more protection for the VANET systems. An effective and safe method of outsourcing is suggested, which reduces computation costs by achieving data security using a homomorphic mapping based on the conjugate operation of matrices. This research proposes a VANET-based data outsourcing system to fix the issues.… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 3111-3138, 2024, DOI:10.32604/cmc.2024.048408
(This article belongs to the Special Issue: Intelligent Detection Methods for AI-Powered Healthcare and Enhanced Medical Insights)
Abstract In the era of advanced machine learning techniques, the development of accurate predictive models for complex medical conditions, such as thyroid cancer, has shown remarkable progress. Accurate predictive models for thyroid cancer enhance early detection, improve resource allocation, and reduce overtreatment. However, the widespread adoption of these models in clinical practice demands predictive performance along with interpretability and transparency. This paper proposes a novel association-rule based feature-integrated machine learning model which shows better classification and prediction accuracy than present state-of-the-art models. Our study also focuses on the application of SHapley Additive exPlanations (SHAP) values as a powerful tool for explaining… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 3139-3173, 2024, DOI:10.32604/cmc.2024.047392
Abstract The Message Passing Interface (MPI) is a widely accepted standard for parallel computing on distributed memory systems. However, MPI implementations can contain defects that impact the reliability and performance of parallel applications. Detecting and correcting these defects is crucial, yet there is a lack of published models specifically designed for correcting MPI defects. To address this, we propose a model for detecting and correcting MPI defects (DC_MPI), which aims to detect and correct defects in various types of MPI communication, including blocking point-to-point (BPTP), nonblocking point-to-point (NBPTP), and collective communication (CC). The defects addressed by the DC_MPI model include illegal… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 3175-3192, 2024, DOI:10.32604/cmc.2023.042873
(This article belongs to the Special Issue: Trends in Machine Learning and Internet of Things for Industrial Applications)
Abstract Electricity theft is a widespread non-technical issue that has a negative impact on both power grids and electricity users. It hinders the economic growth of utility companies, poses electrical risks, and impacts the high energy costs borne by consumers. The development of smart grids is crucial for the identification of power theft since these systems create enormous amounts of data, including information on client consumption, which may be used to identify electricity theft using machine learning and deep learning techniques. Moreover, there also exist different solutions such as hardware-based solutions to detect electricity theft that may require human resources and… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 3193-3209, 2024, DOI:10.32604/cmc.2023.043873
Abstract Super-resolution techniques are employed to enhance image resolution by reconstructing high-resolution images from one or more low-resolution inputs. Super-resolution is of paramount importance in the context of remote sensing, satellite, aerial, security and surveillance imaging. Super-resolution remote sensing imagery is essential for surveillance and security purposes, enabling authorities to monitor remote or sensitive areas with greater clarity. This study introduces a single-image super-resolution approach for remote sensing images, utilizing deep shearlet residual learning in the shearlet transform domain, and incorporating the Enhanced Deep Super-Resolution network (EDSR). Unlike conventional approaches that estimate residuals between high and low-resolution images, the proposed approach… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 3211-3237, 2024, DOI:10.32604/cmc.2023.043935
Abstract The Kingdom of Saudi Arabia (KSA) has achieved significant milestones in cybersecurity. KSA has maintained solid regulatory mechanisms to prevent, trace, and punish offenders to protect the interests of both individual users and organizations from the online threats of data poaching and pilferage. The widespread usage of Information Technology (IT) and IT Enable Services (ITES) reinforces security measures. The constantly evolving cyber threats are a topic that is generating a lot of discussion. In this league, the present article enlists a broad perspective on how cybercrime is developing in KSA at present and also takes a look at some of… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 3239-3259, 2024, DOI:10.32604/cmc.2024.046314
Abstract Traditional clustering algorithms often struggle to produce satisfactory results when dealing with datasets with uneven density. Additionally, they incur substantial computational costs when applied to high-dimensional data due to calculating similarity matrices. To alleviate these issues, we employ the KD-Tree to partition the dataset and compute the K-nearest neighbors (KNN) density for each point, thereby avoiding the computation of similarity matrices. Moreover, we apply the rules of voting elections, treating each data point as a voter and casting a vote for the point with the highest density among its KNN. By utilizing the vote counts of each point, we develop… More >
 Open Access
Open Access
REVIEW
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 3261-3298, 2024, DOI:10.32604/cmc.2024.044890
Abstract This study comprehensively examines the current state of deep learning (DL) usage in indoor positioning. It emphasizes the significance and efficiency of convolutional neural networks (CNNs) and recurrent neural networks (RNNs). Unlike prior studies focused on single sensor modalities like Wi-Fi or Bluetooth, this research explores the integration of multiple sensor modalities (e.g., Wi-Fi, Bluetooth, Ultra-Wideband, ZigBee) to expand indoor localization methods, particularly in obstructed environments. It addresses the challenge of precise object localization, introducing a novel hybrid DL approach using received signal information (RSI), Received Signal Strength (RSS), and Channel State Information (CSI) data to enhance accuracy and stability.… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 3299-3314, 2024, DOI:10.32604/cmc.2024.047811
Abstract Deep neural network-based relational extraction research has made significant progress in recent years, and it provides data support for many natural language processing downstream tasks such as building knowledge graph, sentiment analysis and question-answering systems. However, previous studies ignored much unused structural information in sentences that could enhance the performance of the relation extraction task. Moreover, most existing dependency-based models utilize self-attention to distinguish the importance of context, which hardly deals with multiple-structure information. To efficiently leverage multiple structure information, this paper proposes a dynamic structure attention mechanism model based on textual structure information, which deeply integrates word embedding, named… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 3315-3331, 2024, DOI:10.32604/cmc.2024.046501
(This article belongs to the Special Issue: Machine Vision Detection and Intelligent Recognition)
Abstract Advances in machine vision systems have revolutionized applications such as autonomous driving, robotic navigation, and augmented reality. Despite substantial progress, challenges persist, including dynamic backgrounds, occlusion, and limited labeled data. To address these challenges, we introduce a comprehensive methodology to enhance image classification and object detection accuracy. The proposed approach involves the integration of multiple methods in a complementary way. The process commences with the application of Gaussian filters to mitigate the impact of noise interference. These images are then processed for segmentation using Fuzzy C-Means segmentation in parallel with saliency mapping techniques to find the most prominent regions. The… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 3333-3353, 2024, DOI:10.32604/cmc.2024.049254
(This article belongs to the Special Issue: Unveiling the Role of AIGC, Large Models, and Human - Centric Insights in Digital Defense)
Abstract Author Profiling (AP) is a subsection of digital forensics that focuses on the detection of the author’s personal information, such as age, gender, occupation, and education, based on various linguistic features, e.g., stylistic, semantic, and syntactic. The importance of AP lies in various fields, including forensics, security, medicine, and marketing. In previous studies, many works have been done using different languages, e.g., English, Arabic, French, etc. However, the research on Roman Urdu is not up to the mark. Hence, this study focuses on detecting the author’s age and gender based on Roman Urdu text messages. The dataset used in this… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 3355-3372, 2024, DOI:10.32604/cmc.2024.048706
(This article belongs to the Special Issue: Deep Learning in Computer-Aided Diagnosis Based on Medical Image)
Abstract In addressing the challenge of motion artifacts in Positron Emission Tomography (PET) lung scans, our study introduces the Triple Equivariant Motion Transformer (TEMT), an innovative, unsupervised, deep-learning-based framework for efficient respiratory motion correction in PET imaging. Unlike traditional techniques, which segment PET data into bins throughout a respiratory cycle and often face issues such as inefficiency and overemphasis on certain artifacts, TEMT employs Convolutional Neural Networks (CNNs) for effective feature extraction and motion decomposition.TEMT’s unique approach involves transforming motion sequences into Lie group domains to highlight fundamental motion patterns, coupled with employing competitive weighting for precise target deformation field generation.… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 3373-3395, 2024, DOI:10.32604/cmc.2024.048656
(This article belongs to the Special Issue: Metaheuristic-Driven Optimization Algorithms: Methods and Applications)
Abstract Accurate wind power forecasting is critical for system integration and stability as renewable energy reliance grows. Traditional approaches frequently struggle with complex data and non-linear connections. This article presents a novel approach for hybrid ensemble learning that is based on rigorous requirements engineering concepts. The approach finds significant parameters influencing forecasting accuracy by evaluating real-time Modern-Era Retrospective Analysis for Research and Applications (MERRA2) data from several European Wind farms using in-depth stakeholder research and requirements elicitation. Ensemble learning is used to develop a robust model, while a temporal convolutional network handles time-series complexities and data gaps. The ensemble-temporal neural network… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 3397-3416, 2024, DOI:10.32604/cmc.2024.046265
Abstract A new era of data access and management has begun with the use of cloud computing in the healthcare industry. Despite the efficiency and scalability that the cloud provides, the security of private patient data is still a major concern. Encryption, network security, and adherence to data protection laws are key to ensuring the confidentiality and integrity of healthcare data in the cloud. The computational overhead of encryption technologies could lead to delays in data access and processing rates. To address these challenges, we introduced the Enhanced Parallel Multi-Key Encryption Algorithm (EPM-KEA), aiming to bolster healthcare data security and facilitate… More >
 Open Access
Open Access
ARTICLE
CMC-Computers, Materials & Continua, Vol.79, No.2, pp. 3417-3433, 2024, DOI:10.32604/cmc.2024.049992
(This article belongs to the Special Issue: Metaheuristics, Soft Computing, and Machine Learning in Image Processing and Computer Vision)
Abstract This paper introduces an intelligent computational approach for extracting salient objects from images and estimating their distance information with PTZ (Pan-Tilt-Zoom) cameras. PTZ cameras have found wide applications in numerous public places, serving various purposes such as public security management, natural disaster monitoring, and crisis alarms, particularly with the rapid development of Artificial Intelligence and global infrastructural projects. In this paper, we combine Gauss optical principles with the PTZ camera’s capabilities of horizontal and pitch rotation, as well as optical zoom, to estimate the distance of the object. We present a novel monocular object distance estimation model based on the… More >